What is social engineering?
Social engineering consists of numerous methods. The basic definition of social engineering is the psychological manipulation of others into divulging confidential information or carrying out certain actions. It is therefore distinct from conventional hacking attacks due to the fact that it plays on people’s natural tendency to trust as well as on their credulity and lack of awareness. The aim is usually to extract sensitive data from companies or individuals. Now that the meaning of a social engineering attack is clear, it is crucial to become familiar with social engineering attack techniques and prevention methods. This prevents data leaking out of a company by making employees aware of the threats.
Companies use lots of different tools to protect themselves against cybercrime (e. g. anti-virus software), but the weakest point in an IT security system is usually the human being. Social engineering specialists are excellent psychologists. They are able to manipulate the victim and use clever arguments and formulations. Whatever the size of your business, it is essential to educate employees about threats and the importance and value of data.
Social engineering: Examples
One of the many social engineering methods is pretexting. The attackers conduct thorough research on the victim (which in the age of social media is not so difficult). Then they can, for example, call claiming to be a representative of a company offering excellent BaaS solutions. They use phrases that awaken the caller’s interest (e.g. special deals). They then proceed to extract the necessary information by asking relevant questions, for example: "What server does the company use?" or "Where has the company stored data backups so far?". The final stage is to end the conversation, possibly by quoting a very high price so that the victim can reply that they are not interested in the offer.
Emotions are very often used when executing a social engineering attack. Under their influence, people tend to make irrational decisions. The sense of urgency makes the victim feel time pressure. This can be achieved by offering a reward only if the victim decides within a certain amount of time. Establishing trust is the basis of the whole process. It is for this reason that the attacker conducts thorough research on a company or individual.
Other social engineering methods
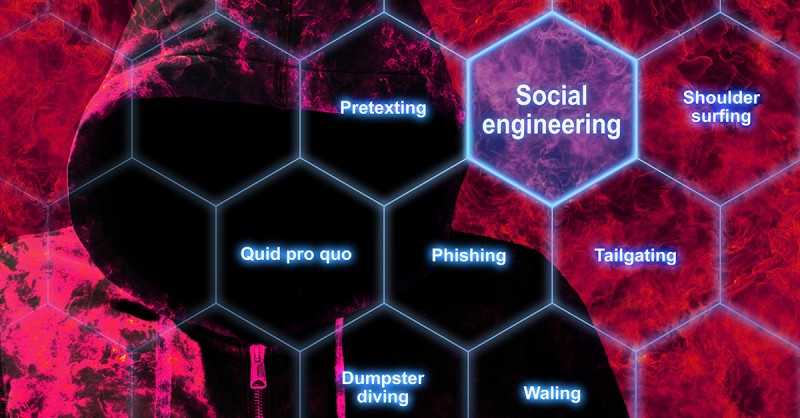
However, there are many more social engineering examples. These can be:
- Phishing: The aim is to make the email recipient believe it is something they need or have been waiting for. The email may include dangerous links or attachments containing virus software. Types of phishing also include spear phishing and whaling.
- Baiting: This is very similar to phishing. However, it uses bait to make the victim download malware. This can take place online or in the form of a package with a CD or USB stick. For example, in 2018, several U.S. state and local government agencies received envelopes with CDs and a letter with confusing content. Victims inserted the CDs into their computers out of curiosity and thus installed the malware. 1
- Shoulder surfing: This method involves stealing data (i.e. passwords) by looking “over the shoulder” when the victim is using their laptop or other device (on a mobile phone or even at an ATM). Awareness of the threat is particularly important for remote working companies, where employees often use their work devices in public places.
- Tailgating: This method involves physically getting entry into protected areas, like a company’s HQ, behind a person who has access. The criminal can impersonate a delivery driver and wait outside the building. When the victim opens the door, they ask him to hold it and thus get inside. To avoid such cases, it is extremely important to properly educate employees and to ensure physical security.
- Dumpster diving: In this case, the criminal is looking for important information in a rubbish bin. Many companies take great care with the security of virtual data, simply forgetting the basics. This is why it is so important to always use paper shredders, which can be located in different places within the office for convenience.
- Quid pro quo: With this method, the attacker calls random phone numbers claiming to be from tech support. Occasionally, of course, they run into a victim who just happened to need it. They offer “help”, gaining access to the computer and being able to install malicious software.
Social engineering prevention
To prevent such attacks, there are several social engineering and cyber security measures to bear in mind:
- Training of employees on social engineering: As we have already mentioned, one of the most important aspects of social engineering prevention is risk awareness. It is therefore essential to organise staff workshops and educate them on the value of data. If your prefer security experts to inform this training, ALSO offers security solutions.
- Putting employees to the test: Occasionally, it’s a good idea to put employees through a test to see if they would do the right things in the event of a real attack. Do they switch off their monitors when they leave their desks? Are there any important documents on their desks? What will they do if an unknown number calls and impersonates someone offering services the company is looking for? Answering these questions will help ensure that each person on the team is aware of what to do.
- Multi-factor authentication: Even a strong password is not always enough. It is better not to rely on single factor authentication for important data. In addition to passwords, multi-factor verification can include fingerprint scanning, security questions, or SMS codes.
-------------------------------------
However, there are many more social engineering examples. These can be:
- Phishing: The aim is to make the email recipient believe it is something they need or have been waiting for. The email may include dangerous links or attachments containing virus software. Types of phishing also include: spear phishing and whaling.
- Baiting: This is very similar to phishing. However, it uses bait to make the victim download malware. This can take place online or in the form of a package with a CD or USB stick. For example, in 2018, several U.S. state and local government agencies received envelopes with CDs and a letter with confusing content. Victims inserted the CDs into their computers out of curiosity and thus installed the malware. 1
- Shoulder surfing: This method involves stealing data (i.e. passwords) by looking “over the shoulder” when the victim is using their laptop or other device (on a mobile phone or even at an ATM). Awareness of the threat is particularly important for remote working companies, where employees often use their work devices in public places.
- Tailgating: This method involves physically getting entry into protected areas, like a company’s HQ, behind a person who has access. The criminal can impersonate a delivery driver and wait outside the building. When the victim opens the door, they ask him to hold it and thus get inside. To avoid such cases, it is extremely important to properly educate employees and to ensure physical security.
- Dumpster diving: In this case, the criminal is looking for important information in a rubbish bin. Many companies take great care with the security of virtual data, simply forgetting the basics. This is why it is so important to always use paper shredders, which can be located in different places within the office for convenience.
- Quid pro quo: With this method, the attacker calls random phone numbers claiming to be from tech support. Occasionally, of course, they run into a victim who just happened to need it. They offer “help”, gaining access to the computer and being able to install malicious software.
Social engineering prevention
To prevent such attacks, there are several important aspects to bear in mind:
- Training of employees on social engineering: As we have already mentioned, one of the most important aspects of social engineering prevention is risk awareness. It is therefore essential to organise staff workshops and educate them on the value of data.
- Putting employees to the test: Occasionally, it’s a good idea to put employees through a test to see if they would do the right things in the event of a real attack. Do they switch off their monitors when they leave their desks? Are there any important documents on their desks? What will they do if an unknown number calls and impersonates someone offering services the company is looking for? Answering these questions will help ensure that each person on the team is aware of what to do.
- Multi-factor authentication: Even a strong password is not always enough. It is better not to rely on single factor authentication for important data. In addition to passwords, multi-factor verification can include fingerprint scanning, security questions, or SMS codes.