we've got your back

The consequences of inadequate cybersecurity measures can be severe:
- Disruption to business operations
- Stolen intellectual property
- High costs
- Reputational damage
With cyberthreats increasing exponentially in quantity and sophistication, your clients need to know exactly how to best protect their operations and digital assets.
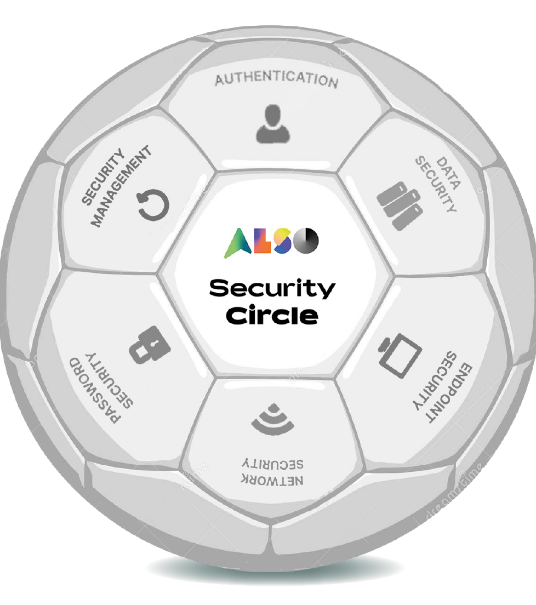
the ALSO SECURITY CIRCLE
Our ALSO Security Circle identifies potential points of entry and protects your customer’s IT infrastructure.
- Authentication – Secure user account logins
- Backup – Data loss prevention and recovery
- Data Security – Prevent unauthorized access, destruction, and distribution of data
- Endpoint Security – Policy-based protection against known and unknown threats
- Mobile Management – Protect and manage mobile devices
- Network Security – Protect internal and external network traffic
- Password Security – Management of system accounts
- Security Awareness – Cybersecurity education for users
- Security Management – Unified monitoring of IT infrastructure
- System Management – Complete inventory control of servers, devices, and workstations