Businesses are experiencing an increase in both the volume and sophistication of cyberattacks. Rapid technological adoption and the shift to hybrid work have posed a greater risk for small and medium-sized customers (learn more about how SMBs can protect themselves from hackers) that need to contend with budget constraints and gaps in specialized security skills.
This case study is intended to better reflect the current Azure security challenges. We will share a customer story that highlights the security gaps and the problems that can arise from those, as well as how to manage the risks.
Problem
Unprotected or inadequately protected credentials are low-hanging fruit for hackers. They can be stolen using phishing techniques or purchased on the dark web. Without an additional level of authentication, hackers can access and gain control over Azure resources. Those resources can then be used for various tasks such as mining cryptocurrency or running denial of service (DoS) attacks.
Anatomy
Attacks tend to be fully automated and do not require significant human resources. Multiple versions of attack scripts are present on the dark web and don’t require a significant initial investment. In most cases, we are talking about drive-by attacks not targeting specific customers or tenants as each one (Azure subscription) has the same value for attackers.
In this example, end-customer credentials were exposed and used to gain access to the Azure portal. An external user was then invited and granted privileged account rights.
Consequence
After the provisioning of unauthorized resources, the consumption spiked to 100K EUR per day. The attacker rolled out compute resources reaching close to 100% of the default CSP quota and multiplied it in more than 60 regions. Such extreme consumption costs are a huge problem even for the biggest customers and for some can be fatal, leading to insolvency for the end customer and bad debt for the partner.
Prevention
Basic cybersecurity hygiene can protect against 98% of attacks. Enabling technologies like multi-factor authentication reduces the risk of unauthorized access. Even after the successful initial credential theft, it reduces the risk to be used to gain control over the Azure subscription.
Solution
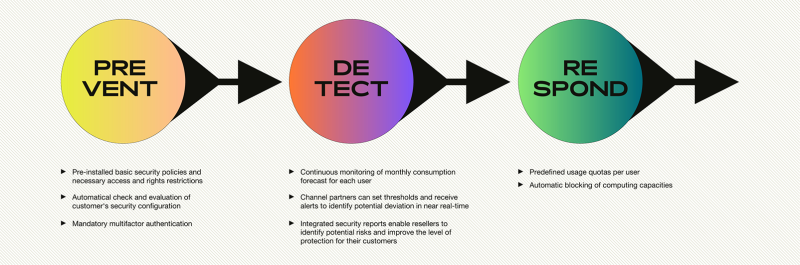
ALSO approach: A single-layer approach cannot provide full complete protection for the customer. It’s therefore recommended to use a multi-layer approach. That includes security technologies, tools, and processes. All concerned parties that have access to the customer Azure subscription must make joint efforts to minimize exposure to fraudulent attacks. To support our partner and customers in this effort ALSO has developed a set of fraud protection tools available via the ALSO Cloud Marketplace:
- Microsoft Security Report helps partners to have an overview of their customers’ security state and identify potential security gaps.
- Azure policies help to prevent unintentional or unauthorized use of computing resources with high cost, used for most fraud cases.
- Azure consumption forecast and thresholds can be used to be notified of forecasted consumption exceeding the partner-set threshold limit.
- MFA validation prevents granting access rights to users, without MFA enabled, in the ordering process of the Azure subscription.
To respond to the recent increase in Azure fraud cases, we are educating our partners on how to use our tools and how to raise customer awareness. We support our partners by proactively monitoring and responding to potential threats, as well as mitigating the attacks.
Our internally developed tools allow tracking Azure usage and consumption patterns, flagging suspicious subscriptions and associated resources. This allows us to identify fraud cases in an early stage and reduce the damage multiple times.
Learn more about how to evaluate and reduce account security risks with ALSO’s solutions!