WE'VE GOT YOUR BACK

Cybersecurity is a high-stakes game in a dark arena against dangerous opponents.
There’s no end, halftime, or pause, and vulnerabilities are endlessly probed from all sides. There’s a lot on the line, and the consequences of inadequate security can be severe.
- Reputational damage
- Increased costs
- Disruption to business operations
- Stolen intellectual property
- Financial loss
With cyberthreats increasing exponentially in quantity and sophistication, your customers need to know what they’re up against and how to best protect their operations and digital assets.
Get an experienced team in your corner with a defensive line-up that leaves no gaps. Put yourself in a winning position.
We’re on your side

We’re committed, and we’ve got a game plan.
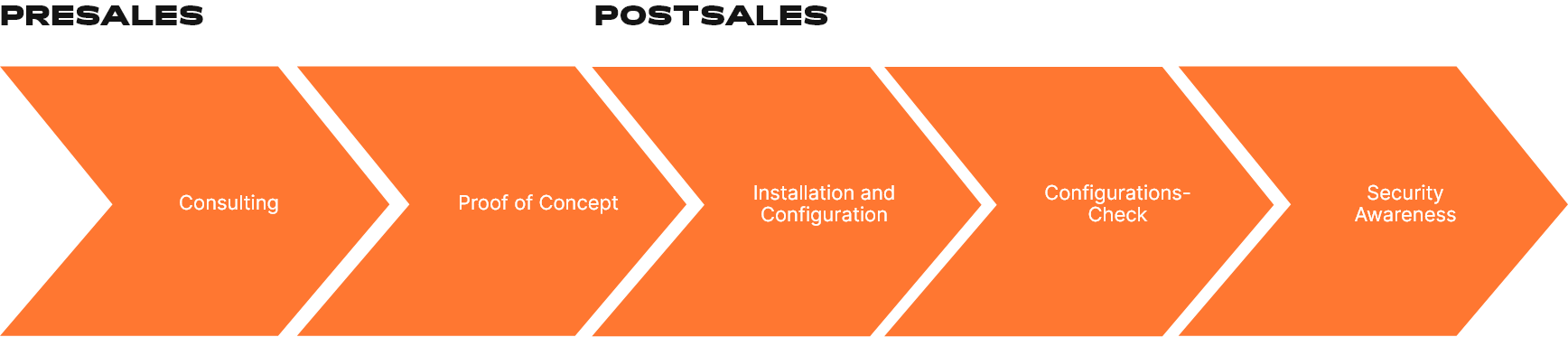
We’ll help you develop, promote, and support your cybersecurity portfolio. It’s an end-to-end strategy.
- Independent, vendor agnostic consultation
- Training
- Sales
- Proof of concept
- Installation and configuration
- Professional services
- Support
Build a winning defensive strategy.
In the cybersecurity game, we mean business

Cybersecurity isn't just essential for business; it's vital for YOUR business. Put together a world-class defensive lineup. Command of best-in-class cybersecurity solutions and services. Protect your clients’ business goals with robust defenses specifically designed and configured to meet their needs.
Let our experts introduce you to the complete defensive lineup. Learn when and where to put them into play. Cybersecurity solutions are determined by an organization's threat level, IT complexity, and training capacity.
Profit by securing your customers' business goals.
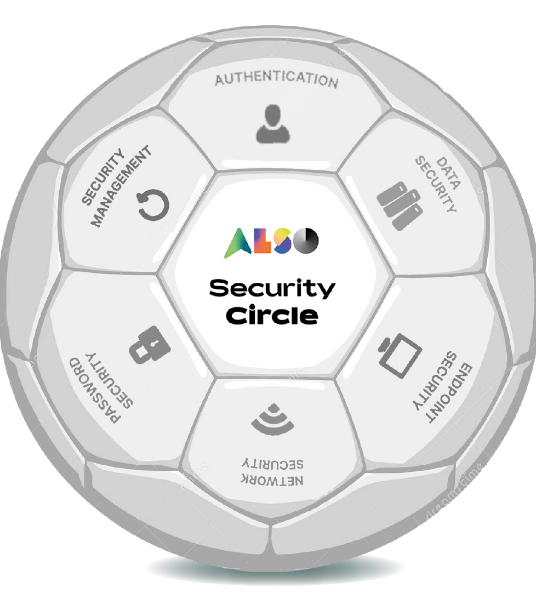
THE ALSO SECURITY CIRCLE
Our ALSO Security Circle is your comprehensive cybersecurity strategy covering the long and short game, covering acute points of entry, and protecting broader IT infrastructure.
- Authentication – Secure user account logins
- Backup – Data loss prevention and recovery
- Data Security – Prevent unauthorized access, destruction, and distribution of data
- Endpoint Security – Policy-based protection against known and unknown threats
- Mobile Management – Protect and manage mobile devices
- Network Security – Protect internal and external network traffic
- Password Security – Management of system accounts
- Security Awareness – Cybersecurity education for users
- Security Management – Unified monitoring of IT infrastructure
- System Management – Complete inventory control of servers, devices, and workstations
Protect business-forward goals and profit. We’ve got your back.
Enter The Game

E-mail Security: Strengthen your customers’ digital shield
E-mails are the lifeblood of modern business communication, but they're also a prime target for cyber threats. As an IT Reseller, the protection of your customers' businesses is paramount. Shield their organizations from email-based attacks with our all-encompassing e-Mail security solutions. Prevent malicious actors from breaching their digital fortresses and ensure secure communication channels.
Discover the power of comprehensive e-Mail security solutions.